Grant yourself access to an Azure Key Vault
Posted 31 Jan 2020
Azure Key Vault is a great way to protect your secrets but while you’re working on ARM templates to deploy your environment you’ll need access to the Key Vault from time to time to verify it’s contents or setup new secrets.
Adding a policy in the Azure Portal
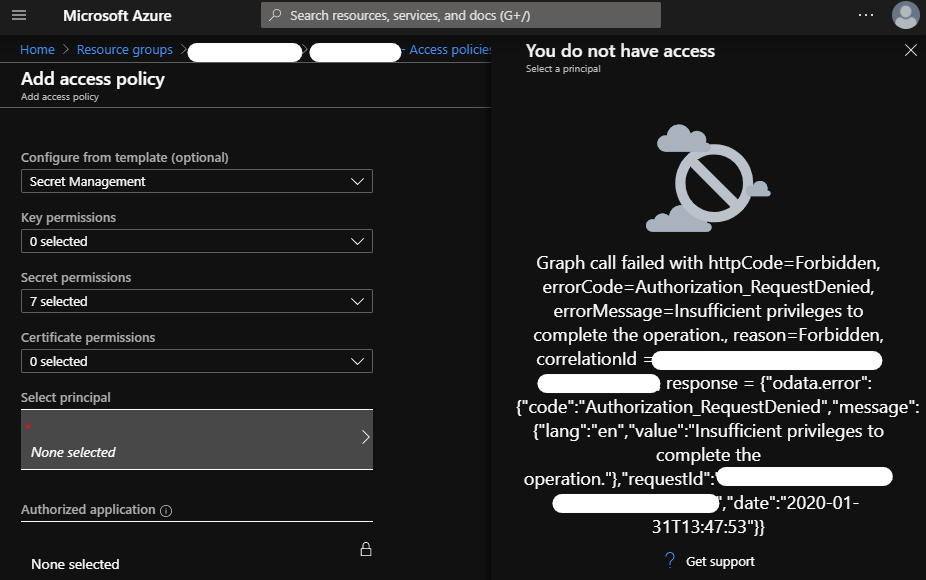
This is easy enough when you have access to Azure Active Directory; you can add a policy to allow yourself into the key vault. Sometimes though, you have to work under stricter conditions where AAD access is not allowed. The Azure portal won't even let you pick your own account:
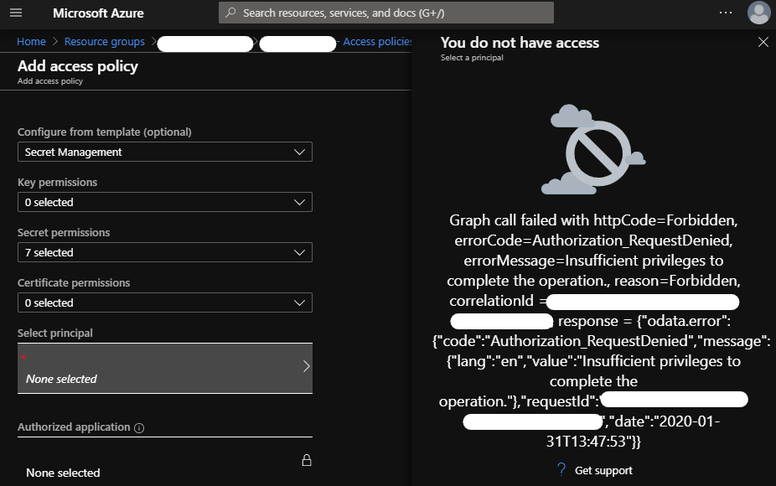
The principal selection dialog will show you an error like:
Graph call failed with httpCode=Forbidden, errorCode=Authorization_RequestDenied, errorMessage=Insufficient privileges to complete the operation., reason=Forbidden
Adding a policy through Azure CLI
You can still grant yourself access with Azure CLI:
az keyvault set-policy –n my-vault –-secret-permissions list get set delete –object-id [my-aad-guid]
Here are the full details on that command.
When you don’t have access to the Azure AD, it’s also a bit tricky to find the object id for your (guest) account. Fortunately, you can find that id using Azure CLI as well:
az ad signed-in-user show --query objectId
Make sure you are logged in using az login and select the right Azure subscription using az account set
Here’s the full PowerShell script:
| param ([Parameter(Mandatory)]$keyvaultname) | |
| $userid = az ad signed-in-user show --query objectId | |
| if($LASTEXITCODE){ | |
| Write-Information "Please login using 'az login' and make sure you select the correct subscription with 'az account'" | |
| } | |
| az keyvault set-policy -n $keyvaultname --secret-permissions backup delete get list purge recover restore set --object-id $userid |