Manage WAF rules for Azure Application Gateway
Posted 12 Apr 2021
Azure Application Gateway is a great way to shield your Azure APIs and WebApps from the big bad internet. The v2 WAF SKU includes powerful Web Application Firewall integration including protection against the common OWASP attacks. The built-in rules are a bit crude though and can cause false positives, resulting unintended blocking.
403 forbidden microsoft-azure-application-gateway/v2
Analysing WAF logs to find blocked requests
To find out what rules are causing request to be blocked I use the following KQL query:
The query lists all the relevant information you need to identify and resolve inadvertent blocking. In the Azure portal, open up the log tab on the App Gateway and execute the query. It should look something like this:
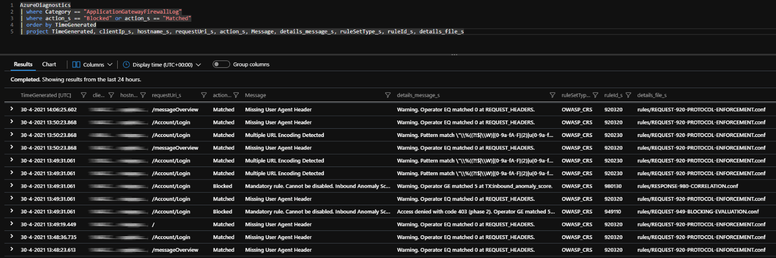
There are multiple requests here getting flagged for different reasons. Too many flags result in requests being block from that source.
Note the last two columns; they list the rule number and section. This will help locate the rules in the Azure Portal or to specify the correct rules in an ARM template.
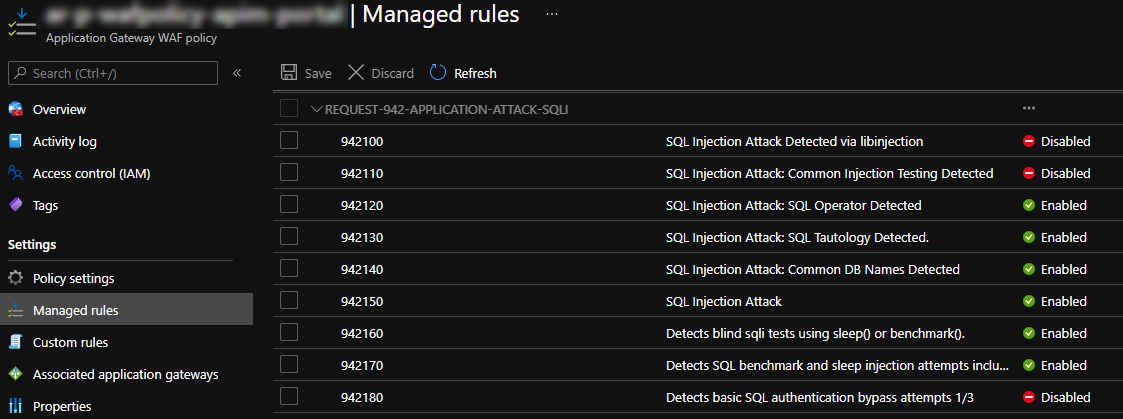
Disable rules
Disabling OWASP rules without proper investigation is probably not a good idea, but some of the rules are... well... a bit crude and can match on things that you consider normal use of your application. For example, I've seen friendly URLs for products match SQL Injection rules. Missing HTTP Accept headers are not an uncommon thing either when 3rd parties integrate with your APIs.
Microsoft provides this guidance on what WAF rules to disable when deploying an Azure API Management instance behind an Azure Application Gateway.
You can disable rules manually in the Azure portal and the query will help you find the right rules.
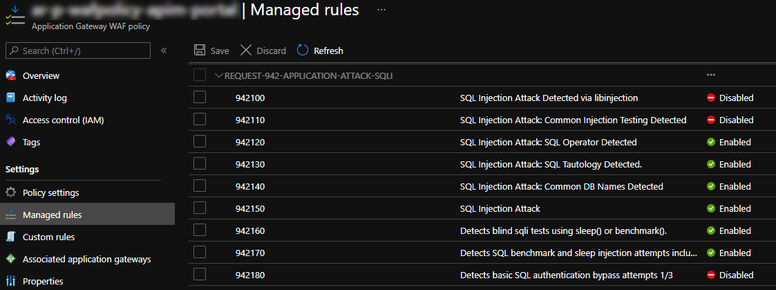
If you're deploying your infra as code, here's how to do that from an ARM template. To make the overrides reusable between different WAF rules I prefer putting them in the variables section:
Then, under the managed rules, set the overrides:
There's full ARM template in this gist